Are you worried that hackers will attack your WordPress website? We wish we could’ve told you not to worry but the truth is WordPress websites are constantly targeted by hackers. This is mainly on account of its popularity as WordPress powers a third of all the websites on the internet.
While WordPress itself is a secure website building platform, it does not function alone. You need plugins and themes to run a WordPress site. Plugins and themes often develop vulnerabilities which hackers exploit to hack a website.
Once they have access to your website, they run all sorts of malicious activities like stealing sensitive information, defrauding customers and displaying illegal content. Meanwhile, you can be blacklisted by Google,or even get suspended by your webhost. All this leads to a loss of visitors and revenue.
While WordPress developers keep the platform secure as it can be, WordPress site owners also need to take measures on their own. In this article, we discuss the most common attacks on WordPress sites and the preventive measures you can take against them.
TL;DR
If you are worried about hackers attacking your WordPress website, you can take website protection measures immediately. You can install our WordPress security plugin MalCare. It will scan and monitor your site every day and block hackers from trying to break in.
Why Is WordPress A Popular Target For Hackers?
WordPress is a website building platform that enables anyone to build websites without knowing how to code. Moreover, WordPress is free of cost.
As a result, the platform is powering over 1.3 billion active sites today.
The downside of all this is that WordPress websites are targeted more than websites built on any other platform.
Now there are multiple ways in which hackers can break into your site. We’ve narrowed it down to the 5 most common ones. We’ll explain what happens and how you can protect your WordPress site against it.
5 Most Common Attacks on WordPress Websites
1. Vulnerable Plugins and Themes
A WordPress site is created using three elements – the core installation, themes and plugins. All three elements have the potential to make a site vulnerable to hacks.
For many years, there hasn’t been any major vulnerability in the WordPress core. It is maintained by a team of highly experienced and qualified developers. They work hard at ensuring the platform is completely secure so you have nothing to worry about there.
However, WordPress plugins and themes are created by third-party developers and they tend to develop WordPress vulnerabilities quite often.
When developers discover any vulnerability, they promptly fix it and release an updated version.
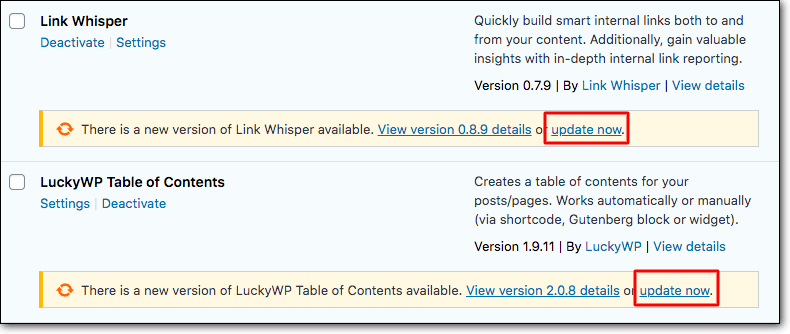
You, the site owner, need to update to the latest version and your site will be secure. It’s important to install such security updates immediately. This is because when developers release an update, they also release the reasons for the update. Thus, the vulnerability is announced to the public.
This means hackers now know that a vulnerability exists. They also know that not all site owners update their sites immediately. So once they find out that a plugin or theme is vulnerable, they program bots and scanners to crawl the internet and find sites that are using them. Knowing exactly what the vulnerability is makes it easy for them to exploit and break in.
How to Protect Your site Against Vulnerable Plugin & Themes
-
- Only use trusted themes and plugins found in the WordPress repository or marketplaces like ThemeForest and Code Canyon.
- Check your plugin list regularly and keep only the ones you use. Delete any ones you don’t need or are inactive.
- Ideally, you should keep only the theme that you are actively using.
- Never use pirated themes and plugins. They usually contain malware that will infect your website.
- Ensure you recognise all the plugins and themes on your site. Sometimes hackers install their own plugins and themes that have website backdoors installed. This gives them a secret access to your site.
2. Brute Force Attacks
To login to your WordPress site, you need to enter your login credentials i.e., a username and password.
Many times, WordPress site owners use usernames and passwords that are easy to remember. Many WordPress users retain the default username ‘admin’. Common passwords include ‘password123’ or ‘1234567’.
Hackers are well aware of this and attack the login page of WordPress sites.

They create a database of commonly used usernames and passwords. Next, they program bots to target WordPress sites and attempt different combinations present in their database.
If your login credentials are weak, the bots have a high chance of guessing it and breaking into your site. This is known as ‘Brute Force Attacks’ and is estimated that they have a 10% success rate!
How to Protect Your site Against Brute Forcing
There are a couple of steps you can take to secure your site against brute force attacks:
-
- By default, your WordPress username is admin. You can change it from admin to something more unique.
- Use a strong WordPress password. We suggest using a passphrase in combination with numerals and symbols such as Birdsofafeather123$.
- Use unique credentials that you have not used on other websites.
- Limit the number of login attempts on your site. This means a WordPress user will have only limited chances to enter the right credentials such as 3 attempts or 5 attempts. After this, they will need to use the ‘forgot password’ option. You can install our MalCare security plugin on your site and it will automatically implement this login protection for you.
- Use twofactor authentication wherein a WordPress user has to enter their credentials along with a one-time password that is generated on their smartphones or sent to their registered email address.
3. Injection Attacks
Almost every website has an input field like a contact form, a site search bar, or a comments section that enables visitors to enter data. Some websites also allow visitors to upload documents and image files.
Usually this data is accepted and sent to your database to be processed and stored. These fields need proper configuration to validate and sanitise the data before it goes to your database. This will ensure that only valid data is accepted. If these measures are lacking, hackers exploit it and enter malicious code.
Let’s take an example of a WordPress site that has a contact form on it. Ideally this form should accept a name, an email address, and a phone number.
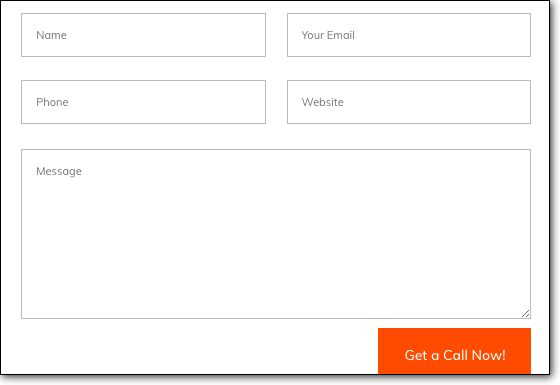
-
- The name field should accept only letters of the alphabet.
- The email address field should accept a valid email address format such as example@mysite.com.
- The phone number field should contain only digits.
Now if these configurations aren’t in place, a hacker can insert malicious scripts such as:
String userLoginQuery = "SELECT user_id, username, password_hash FROM users WHERE username = '" + request.getParameter("user") + "'";
This is a code that’ll command the database to execute certain functions. In this way, hackers are able to run malicious scripts on your site which they can use to gain full control of your site.
The most popular injection attacks on WordPress sites include SQL injection attacks and Cross-Site Scripting.
How to Protect Your Website Against Injection Attacks
-
- Many injection attacks stem from themes and plugins that enable visitor input on your site. We suggest using only trusted themes and plugins. Next, keep your plugins and theme up to date always.
- Control field entries and data submissions. This is technical and would require a developer’s assistance.
- Use a WordPress firewall. If you’ve installed MalCare on your site, it automatically puts up a robust firewall to defend your site against hackers.
4. Phishing and Data Theft
Visitors interact with your website in different ways. Some of them just read your blog posts, others contact you through your contact from, and so on. If you run an ecommerce site then many visitors buy items from your website. This means they need to log into your website and enter credit card information.
When someone enters credit card information to your site, it transfers and stores the information on your site server. This information can be intercepted while it’s being transferred. Moreover, the credit card data can be stolen.
They may also break into your website and pose as you. They send emails or redirect visitors to other websites and trick them into revealing personal data and payment information.
How To Protect Your Site From Phishing and Data Theft
-
- Use an SSL certificate. This will encrypt the data that’s being transferred from and to your site. Even if a hacker intercepts it, they cannot use it as they won’t be able to decipher it. Refer to our guide on using SSL and HTTPS.
- Use a WordPress Security Plugin to receive alerts if there’s any suspicious activity on your website. The plugin will also block hack attempts.
5. Cookie Stealing
Have you noticed that when you log into a site, your browser requests to ‘remember me’ or ‘save password’? This is done so that you don’t have to enter your login credentials every time you want to access a website. You can opt to allow the browser to save your login details.

Browsers can save such data because of cookies. Cookies are tiny bits of data that record a visitor’s interaction with a website. For instance, if you run an online store, your site might track a customer’s journey such as what product they searched for and what they purchased. This data is used in analytics and also advertisers tailor ads to the visitor’s preference. Now, cookies can also store bank details and personal information.
If a hacker is able to steal your website’s cookies, they can access sensitive data of your business and your visitors. They can exploit this data to carry out their malicious acts such as defrauding customers by using their credit card information.
You can read up more on this in our easy guide to Cookie Stealing and Session Hijacking.
How To Protect Your Site From Cookie Stealing and Session Hijacking
-
- Change your WordPress keys and salts regularly. Keys and salts provide secure encryption of the information stored in the browser’s cookies. This measure is technical in nature. We recommend using MalCare’s WordPress hardening feature to change your keys and salts. From the MalCare dashboard, access Security > WordPress hardening > Change WordPress Security Keys and Salts.
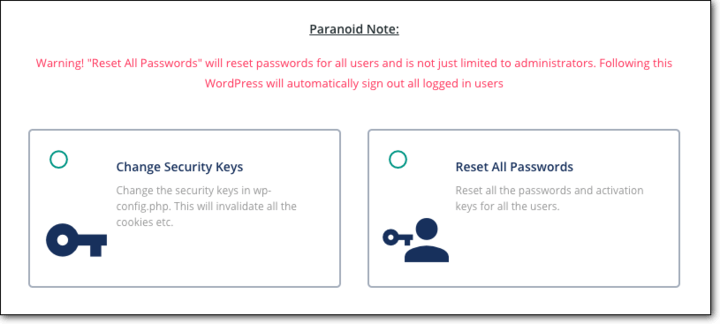
-
- Here too, we recommend installing an SSL certificate to protect your website’s data.
That brings us to an end on the most common WordPress Attacks. Before we wrap up, we’d like to show you a few WordPress hardening measures that will make your site stronger against such attacks.
How To Harden Your WordPress Site Against Attacks
While you can take specific measures to protect your website against certain attacks, there are some overall security measures you can implement on your site for better protection. These are called WordPress hardening measures. We’ve explained it in brief here, but you can read our in-depth guide on WordPress Hardening for more detailed explanations.
1. Disabling the file editor
WordPress has a feature that enables you to edit theme and plugin files directly from the dashboard. Many website owners don’t need this feature, it is mostly used by developers. But if a hacker breaks into your wp-admin dashboard, they can inject malicious code into your theme and plugin files. Thus, if you don’t need this feature, it can be disabled.
2. Disabling plugin or theme installations
When hackers can access your site, they install their own plugins or themes. These plugins and themes are usually malicious and contain backdoors. This gives hackers a secret entry into your site.
Plus, as we mentioned, vulnerable themes and plugins are a top cause of hacked sites. If you have multiple users on your website, they may install a plugin or theme that isn’t secure. This can open up your site to hackers. If you want to avoid this, you can disable plugin and theme installations on your site.
If you don’t regularly install plugins and themes on your site, you can disable the installation option.
3. Limiting login attempts
As we mentioned before, you can limit the number of chances a WordPress user has to enter the correct login credentials to enter the site. This eliminates the risk of brute force attacks.
4. Changing security keys and salts
Keys and salts encrypt the information stored in your browser. So even if a hacker manages to steal your cookies, they can’t decipher it. However, if a hacker accesses these keys and salts, they can use it to decrypt the cookies. Regularly changing your keys and salts can help avoid cookie theft.
5. Blocking PHP execution in unknown folders
There are only certain files and folders on your WordPress site that execute code. Other folders only store information such as your Uploads folder that stores images and videos.
However, when a hacker gains access to your website, they insert php code into random folders or even create their own folders.
You can block such activity by disabling PHP executions in unknown folders.
Implementing these measures requires technical expertise. We don’t recommend doing it manually. It’s much safer and easier to use a plugin like MalCare that lets you do this in just a few clicks.
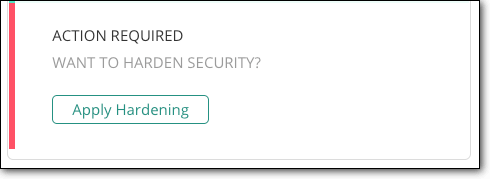
With that, we’re confident your WordPress website is secured and protected against hackers.
Final Thoughts
Hackers have a multitude of ways to break into your WordPress site and they come up with new ones ever so often!
You need to take your security measures to protect your website and ensure it’s safe against hack attacks.
We recommend using our MalCare Security Plugin to secure your WordPress site. It will block hackers and malicious bots from accessing your site. You can rest assured your site is being monitored and protected.
Prevent Hacks With our MalCare Security Plugin!

The post 5 Most Common WordPress Attacks & How To Prevent Them appeared first on MalCare.
Recent Articles By Author
- How To Fix Error “Preventing Possible Attempt To Enumerate Users” (2 Easy Ways)
- Top 5 Shared Hosting Security Risks (And How To Prevent Them)
- Is WordPress Secure as a Website Building Platform?

*** This is a Security Bloggers Network syndicated blog from MalCare authored by Melinda Bartley. Read the original post at: https://www.malcare.com/blog/wordpress-attacks/
'PENTEST' 카테고리의 다른 글
| How to Prevent Cookie Stealing and Hijacking Sessions? (Easiest Guide) (0) | 2021.08.05 |
|---|---|
| Logging out of Wordpress password protected pages with cookie timout? (31) | 2021.08.05 |
| Web Shell PHP Exploit – What, Why & How To Fix (0) | 2021.06.13 |
| How to install Nessusd in Kali linux (0) | 2019.03.10 |
| Scan Websites for Potential Vulnerabilities Using Vega in Kali Linux (0) | 2019.03.10 |
