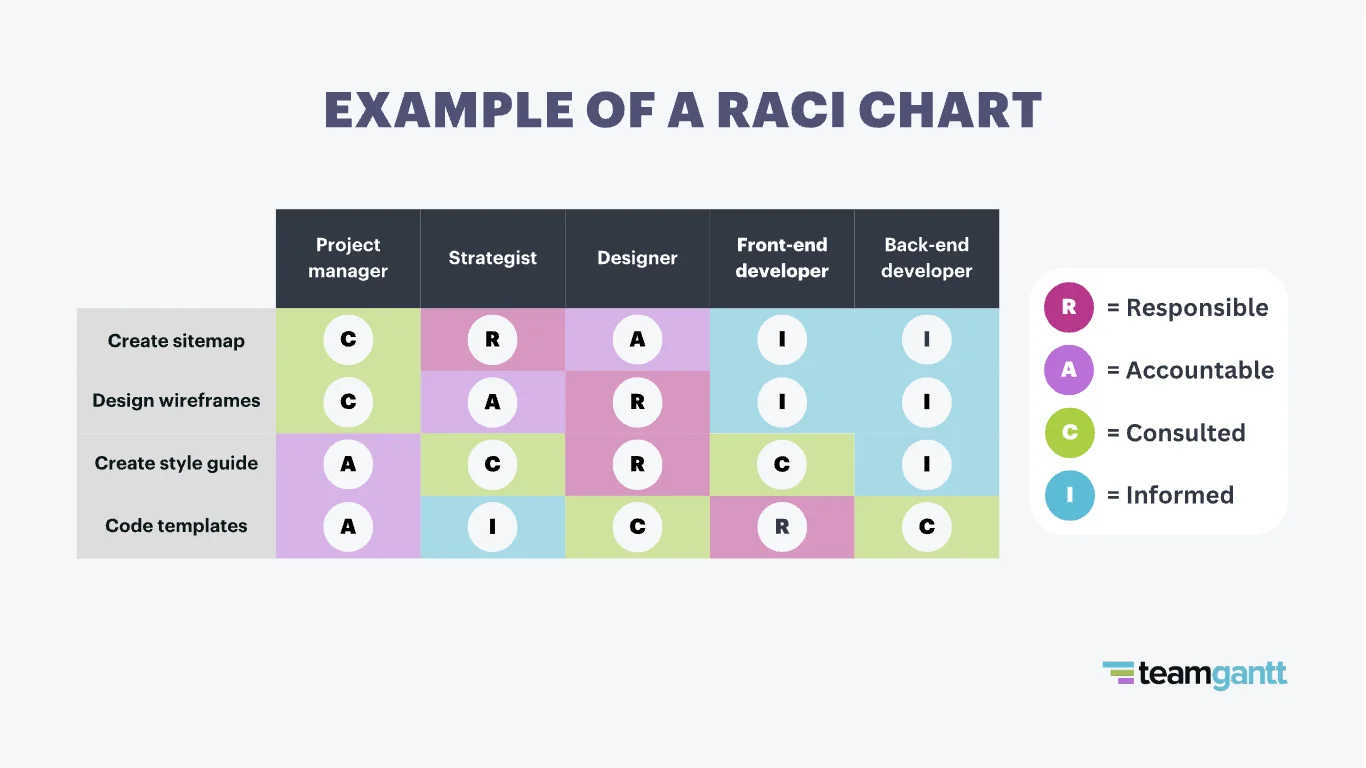
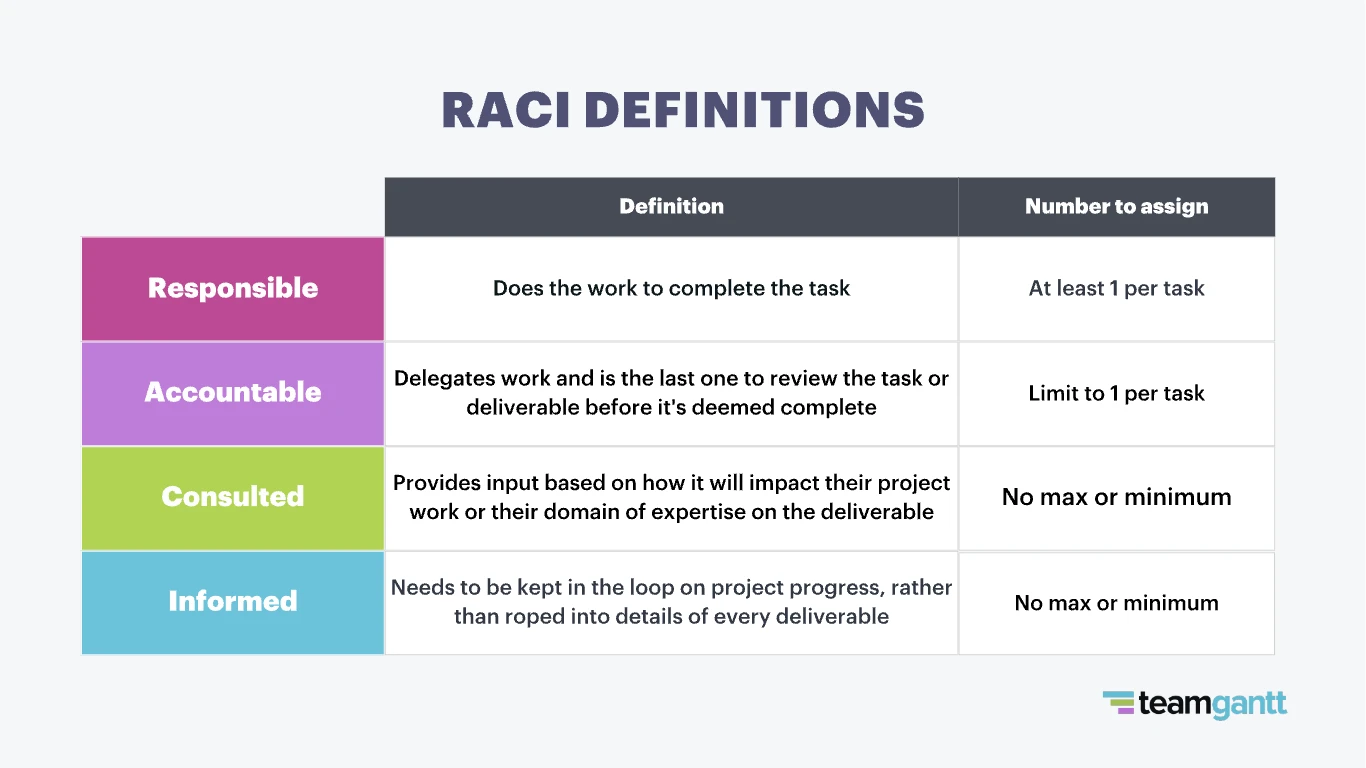
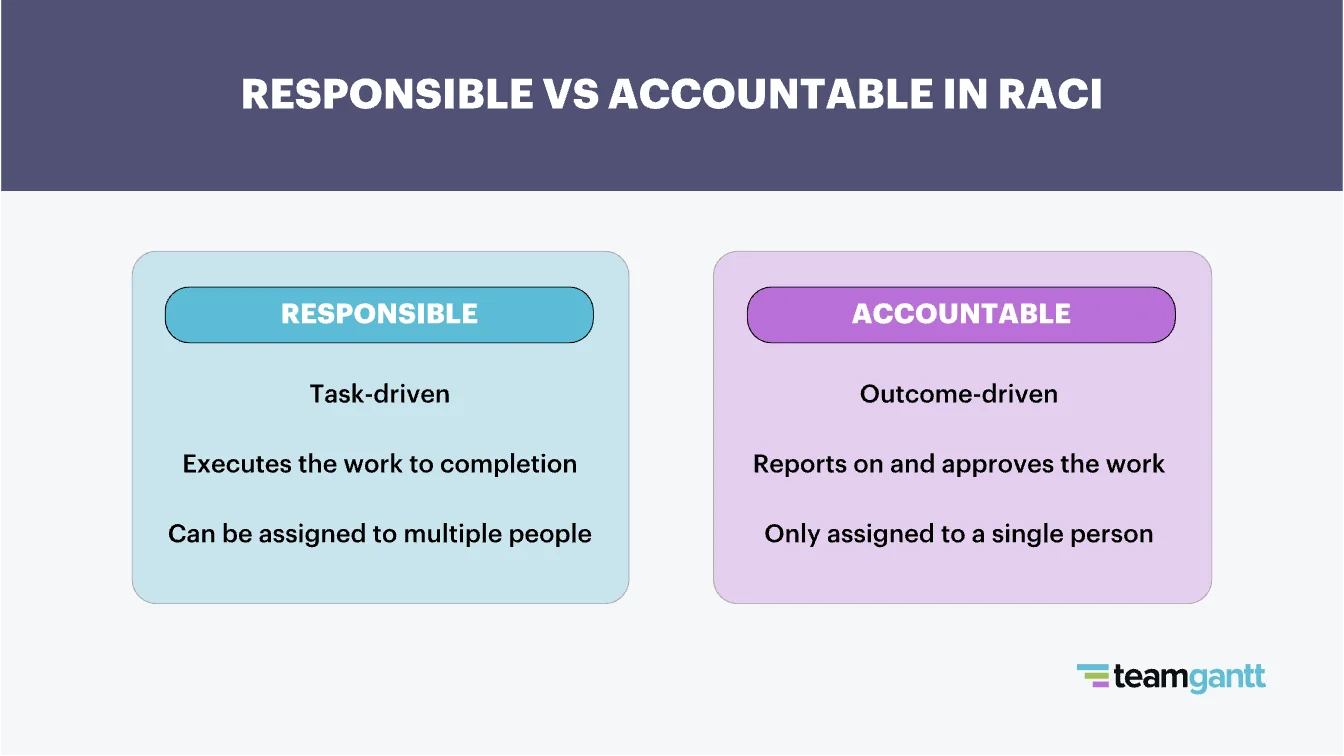
Sometimes changes made to the model or to the ORM may not reflect accurately on the database even after an execution of SchemaUpdate.
If the error actually seems to lack a sensible explanation, try recreating the database (or at least creating a new one) and scaffolding it with SchemaExport.
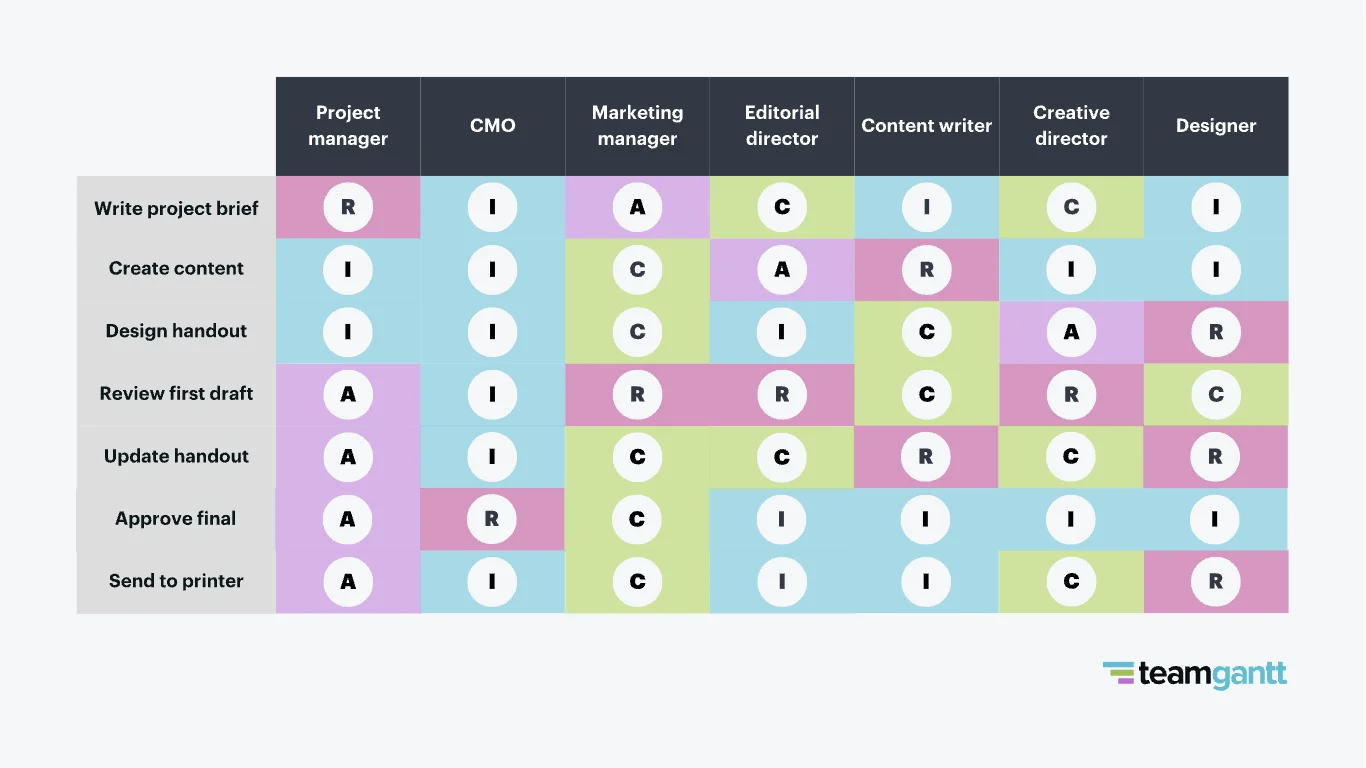
2024-07-23 14:30:43.399 WARN 17560 --- [ault-executor-0] o.h.engine.jdbc.spi.SqlExceptionHelper : SQL Error: 1364, SQLState: HY000
2024-07-23 14:30:43.399 ERROR 17560 --- [ault-executor-0] o.h.engine.jdbc.spi.SqlExceptionHelper : Field 'objectid' doesn't have a default value
2024-07-23 14:30:43.407 ERROR 17560 --- [ault-executor-0] c.c.otp.service.impl.OtpMgrServiceImpl : Error saving OTP Entity:
org.springframework.orm.jpa.JpaSystemException: could not execute statement; nested exception is org.hibernate.exception.GenericJDBCException: could not execute statement
at org.springframework.orm.jpa.vendor.HibernateJpaDialect.convertHibernateAccessException(HibernateJpaDialect.java:331) ~[spring-orm-5.3.27.jar:5.3.27]
at org.springframework.orm.jpa.vendor.HibernateJpaDialect.translateExceptionIfPossible(HibernateJpaDialect.java:233) ~[spring-orm-5.3.27.jar:5.3.27]
at org.springframework.orm.jpa.AbstractEntityManagerFactoryBean.translateExceptionIfPossible(AbstractEntityManagerFactoryBean.java:551) ~[spring-orm-5.3.27.jar:5.3.27]
at org.springframework.dao.support.ChainedPersistenceExceptionTranslator.translateExceptionIfPossible(ChainedPersistenceExceptionTranslator.java:61) ~[spring-tx-5.3.27.jar:5.3.27]
at org.springframework.dao.support.DataAccessUtils.translateIfNecessary(DataAccessUtils.java:242) ~[spring-tx-5.3.27.jar:5.3.27]
at org.springframework.dao.support.PersistenceExceptionTranslationInterceptor.invoke(PersistenceExceptionTranslationInterceptor.java:152) ~[spring-tx-5.3.27.jar:5.3.27]
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) ~[spring-aop-5.3.27.jar:5.3.27]
at org.springframework.data.jpa.repository.support.CrudMethodMetadataPostProcessor$CrudMethodMetadataPopulatingMethodInterceptor.invoke(CrudMethodMetadataPostProcessor.java:174) ~[spring-data-jpa-2.7.12.jar:2.7.12]
at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) ~[spring-aop-5.3.27.jar:5.3.27]
at org.springframework.aop.interceptor.ExposeInvocationInterceptor.invoke(ExposeInvocationInterceptor.java:97) ~[spring-aop-5.3.27.jar:5.3.27]
at org.springframework.aop.framework.ReflectiveMe
종종 ORM 관련되서 맛탱이가 가는 경우가 있는데, 정상적으로 save method 를 실행하지 못하며 신기하게 에러를 뱉는 경우가 있다.
디버깅에서 잡고 찔러봐도 분명히 데이터는 들어가는데, 왜 default value를 저장하는지 모르겠다 하고.
결론은 Stack Overflow 에서처럼 테이블 드랍시키고 다시 만들면 쑤욱 하고 들어간다
https://stackoverflow.com/questions/804514/hibernate-field-id-doesnt-have-a-default-value
Hibernate: "Field 'id' doesn't have a default value"
I'm facing what I think is a simple problem with Hibernate, but can't solve it (Hibernate forums being unreachable certainly doesn't help). I have a simple class I'd like to persist, but keep gett...
stackoverflow.com
'Java > Spring Boot JPA' 카테고리의 다른 글
| [FCM HTTP v1] 400 Bad Request 와 문제 해결 (0) | 2024.10.06 |
|---|---|
| [CORS] setAllowdOrigins method and property (0) | 2024.08.28 |
| Request Body로 보내지는 JSON의 행방 불명 (3) | 2024.05.16 |
| JPA - Field 'id' doesn't have a default value (0) | 2024.05.13 |
| [Spring Batch] 조져보자 meta table (0) | 2024.04.29 |